With the recent natural disasters in Texas, Florida, and Puerto Rico, there seems to be an uptick in fraudulent activity. With that in mind, we bring you a recent blog from our friends at SDN Communications discussing how to spot fraudulent emails and ways to navigate around them. So, without further ado, we present Email spoofing: What it is and how to spot it.
——————————————————————————————————————————————————————-
After the recent hurricanes that struck Texas, Florida and Puerto Rico, there were unsettling reports about fraudsters spoofing caller identification numbers to make scam calls about flood insurance.
In other words, the bad guys disguised their phone numbers to trick the people they called out of information or money.
Despicable, yes. Uncommon, no.
Spoofing attacks come in other forms, too, including texts and emails. Spoofing is even common on social media sites. A fraudster will open an account on Facebook, for example, and copy and use someone else’s information. Then, they’ll try to trick the victim’s friends out of information or money.
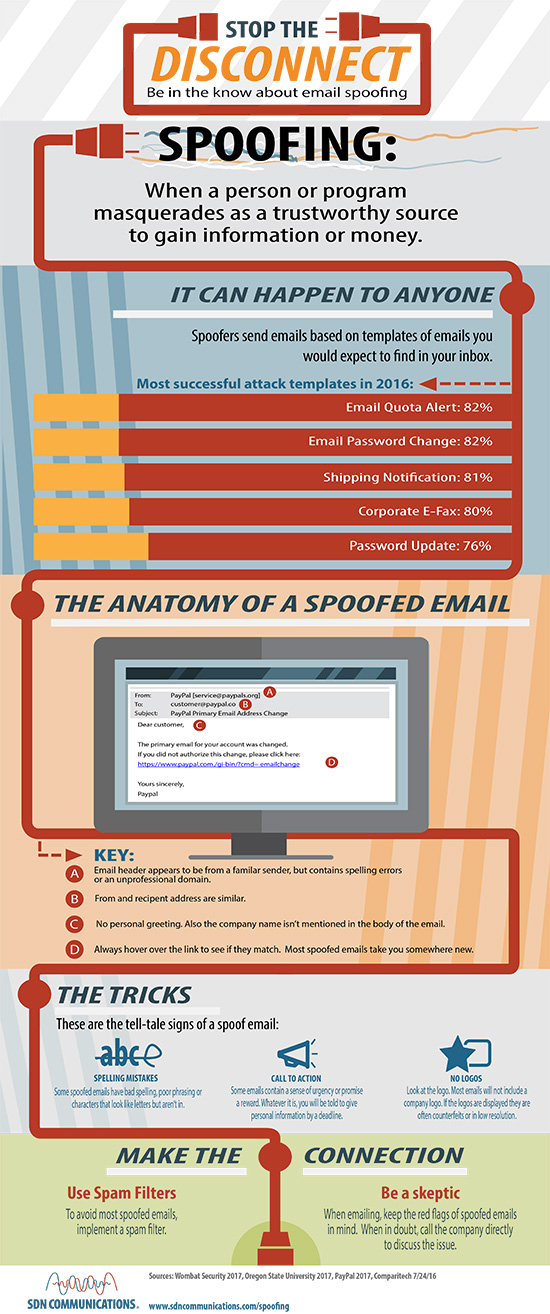
Spoofed email is probably a bigger threat, however, and it can be difficult to detect. Spoofing an email typically refers to when a sender poses as a trustworthy source to get something from the recipient.
“It’s a type of phishing attack where they spoof an email address,” said Chad Pew, manager of IT at SDN Communications in Sioux Falls. “They’re either doing it for financial gain or for information.”
It’s often part of phishing, which are deceitful attempts to gain information or access to a network. The spoofing part is when the fakers disguise their messages to come from a legitimate source. For example, the fraudsters will alter the email’s “from” address.
CEOs and other business executives are frequent targets because they control resources and usually have access to valuable information. However, spoofed emails can target anyone. They aren’t always straight-out requests for information; they might come camouflaged as a bogus alert that encourages action.
Everyone should beware of email headers with spelling errors or messages that look unprofessional and ask for payment or sensitive information. (Check out the anatomy of a spoofed email in the infographic below.)
If you’re in any doubt about the authenticity of a request from a business or an organization, look up the sender’s contact information independently – don’t rely contact information provided in the suspect message. Then, contact the company directly for verification.
You can take other precautions too; a good place to start is using spam filters.
Security experts at SDN and elsewhere also recommend using a strong and different password for every connected device. That way, if one site gets hacked with pilfered information, other sites can’t be easily compromised, too.
Also use two-factor authentication whenever possible so that stealing a password isn’t enough to misuse an account. Hackers also might need a code from a mobile phone to get into your account.
Businesses, in particular, should use tools that filter and protect email access to their networks.
Pew suggests businesses establish an SPF, or Sender Policy Framework, record to help detect email spoofing. It lists in an accessible form which mail servers are permitted to send email on behalf of a domain.
SDN’s spam filtering system stops hundreds, possibly thousands of fraudulent emails every day. Still, emails with deceptive requests can get through the best mechanical protections. Employees are often the last point of defense.
So, in addition to good equipment and policies, business need to invest in good, ongoing training to help employees recognize email threats and other cybersecurity risks. Everyone needs to stay informed and be on guard.
Unfortunately, cybercrime has become so prevalent that it’s a good rule of thumb is to view any emailed or phoned request for personal or corporate information with a healthy degree of suspicion.
SDN has created a simple infographic for you to share with employees to help educate them on how to identify spoofing attempts.